Azure SQL Database transparent data encryption helps protect against the threat of malicious activity by performing real-time encryption and decryption of the database, associated backups, and transaction log files at rest without requiring changes to the application.
TDE encrypts the storage of an entire database by using a symmetric key called Database Encryption Key (DEK). In SQL Database the Database Encryption Key is protected by built-in server certificate. The built-in server certificate is unique for each SQL Database server. If the database is in a GeoDR relationship, it is protected by a different key on each server. If 2 databases are connected on a same server, they share the same built-in certificate. Microsoft automatically rotates these certificates at least every 90 days.
Note: TDE does not provide encryption across communication channels.
When using TDE with SQL Database V12, the server-level certificate stored in the master database is automatically created for you by SQL Database. To move a TDE database on SQL Database you must decrypt the database, move the database, and then re-enable TDE on the Destination Database.
Enable TDE on a Database Using the Portal
- Visit the Azure portal at https://portal.azure.com and sign with your Azure Administrator or contributor account.
- On the left banner, click to BROWSE, and then click SQL Databases.
- With SQL Databases selected in the left pane, click the user database, here in our example I have selected the Sample AdventureWorks2012 Database, as per Image 1.0
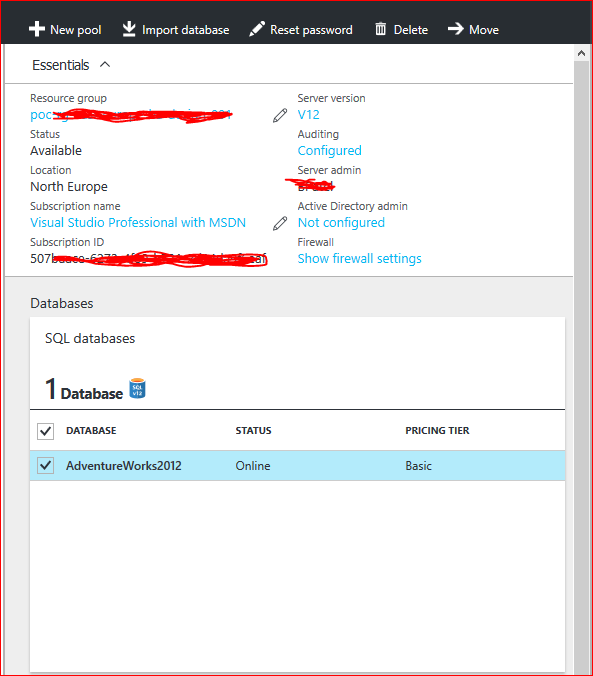
- Click the Transparent Data Encryption part to open the Transparent Data Encryption blade.
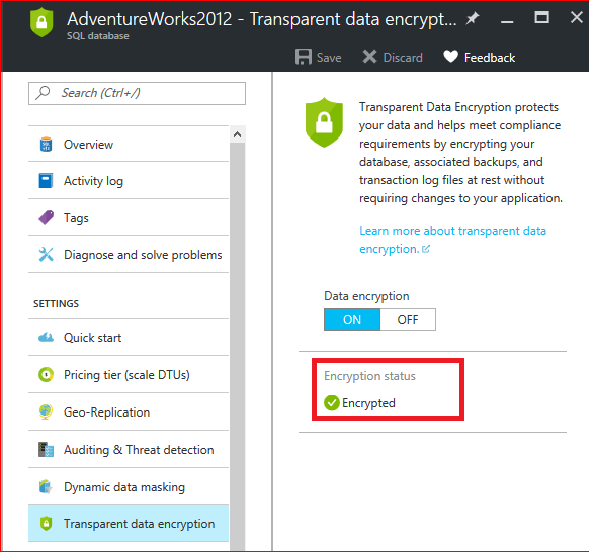
- In the Data Encryption blade, move the Data Encryption button to On.
-
Finally, click Save (at the top of the page) to apply setting. The Encryption status will approximate the progress of the transparent data encryption.

-
Once the encryption completed, you should be able to see the Encryption Status as Encrypted as per the image below.